
A hacker responsible for the $1.4 billion Bybit heist has laundered over 50% of the stolen Ethereum in just five days, pushing THORChain’s transaction volumes to record highs.
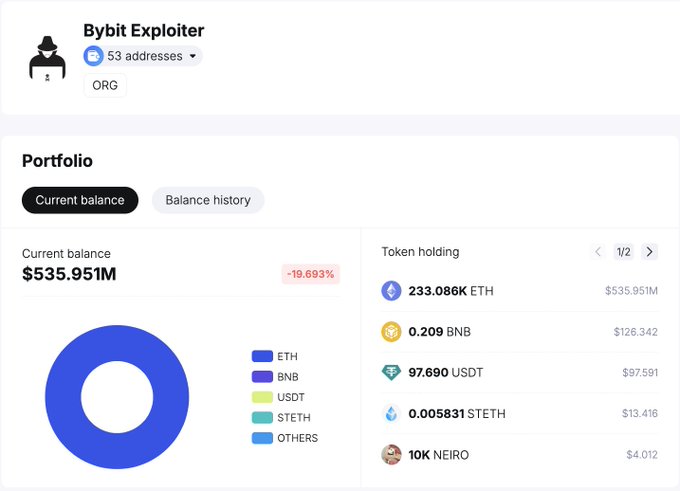
According to blockchain analytics firm Spot On Chain, the attacker moved 266,309 Ethereum (ETH), worth approximately $614 million, at an average rate of 48,420 ETH per day.
If this pace continues, the remaining 233,086 ETH could be fully laundered within the next five days.
The surge in illicit transactions has exposed vulnerabilities in decentralized finance (DeFi) protocols, as THORChain recorded an unprecedented $2.91 billion in transaction volume between Feb. 22 and Feb. 27.
The spike highlights how DeFi platforms can be exploited for large-scale money laundering, raising concerns over regulatory gaps in the crypto industry.
THORChain transaction volumes hit record
THORChain, a decentralised liquidity protocol, has become the primary channel for laundering the stolen Ethereum. Before the attack, THORChain’s average daily transaction volume stood at $80 million.
Since the hacker began moving funds, daily volumes have jumped to $580 million.
The most dramatic spike occurred on Feb. 26, when THORChain processed a record-breaking $859.61 million in swaps, followed by an additional $210 million on Feb. 27, bringing the two-day total past $1 billion.
This unprecedented increase has also generated significant profits for THORChain. The network earned $3 million in fees from the sudden surge in activity, underscoring the financial impact of illicit transactions on DeFi platforms.
The situation raises concerns about the ability of decentralised exchanges to detect and prevent large-scale laundering schemes.
FBI links hack to North Korea
The US Federal Bureau of Investigation (FBI) has officially linked the Bybit hack to North Korean state-sponsored cybercriminals.
In a statement released on Feb. 26, the FBI identified the attack as part of a broader cyber campaign known as “TraderTraitor,” which has been used to target cryptocurrency firms and financial institutions worldwide.
North Korean hacking groups, particularly Lazarus Group, have been linked to multiple high-profile crypto heists in recent years.
The funds stolen in such attacks are often used to finance the country’s weapons programme, making the Bybit hack not just a financial crime but a geopolitical concern.
The rapid laundering of stolen assets through DeFi platforms further complicates efforts to track and recover illicit funds, as decentralized protocols lack the oversight of traditional financial systems.
Attackers exploited the infrastructure provider
Forensic investigations by Sygnia Labs and Verichain have revealed that Bybit’s security infrastructure remained intact despite the breach.
Instead, the vulnerability was traced back to a Safe Wallet developer machine that had been compromised. Attackers exploited this weak link to inject malicious JavaScript code into the Gnosis Safe UI, targeting Bybit’s cold wallet.
This incident highlights a shift in hacker tactics. Rather than directly breaching exchanges, cybercriminals are increasingly targeting infrastructure providers that support major crypto platforms.
While Safe has affirmed that its smart contracts remain secure, the attack underscores the need for enhanced security across the entire crypto ecosystem, including wallet providers and third-party developers.
To mitigate the damage, Bybit has launched a website to track the movement of stolen funds. The exchange is also offering a bounty to any platform or individual who assists in recovering the assets.
With over half of the stolen Ethereum already laundered, the likelihood of full recovery is rapidly diminishing.
The post Bybit theft: Hacker launders over 50% of stolen $1.4B in Ethereum appeared first on Invezz















 English (US) ·
English (US) ·