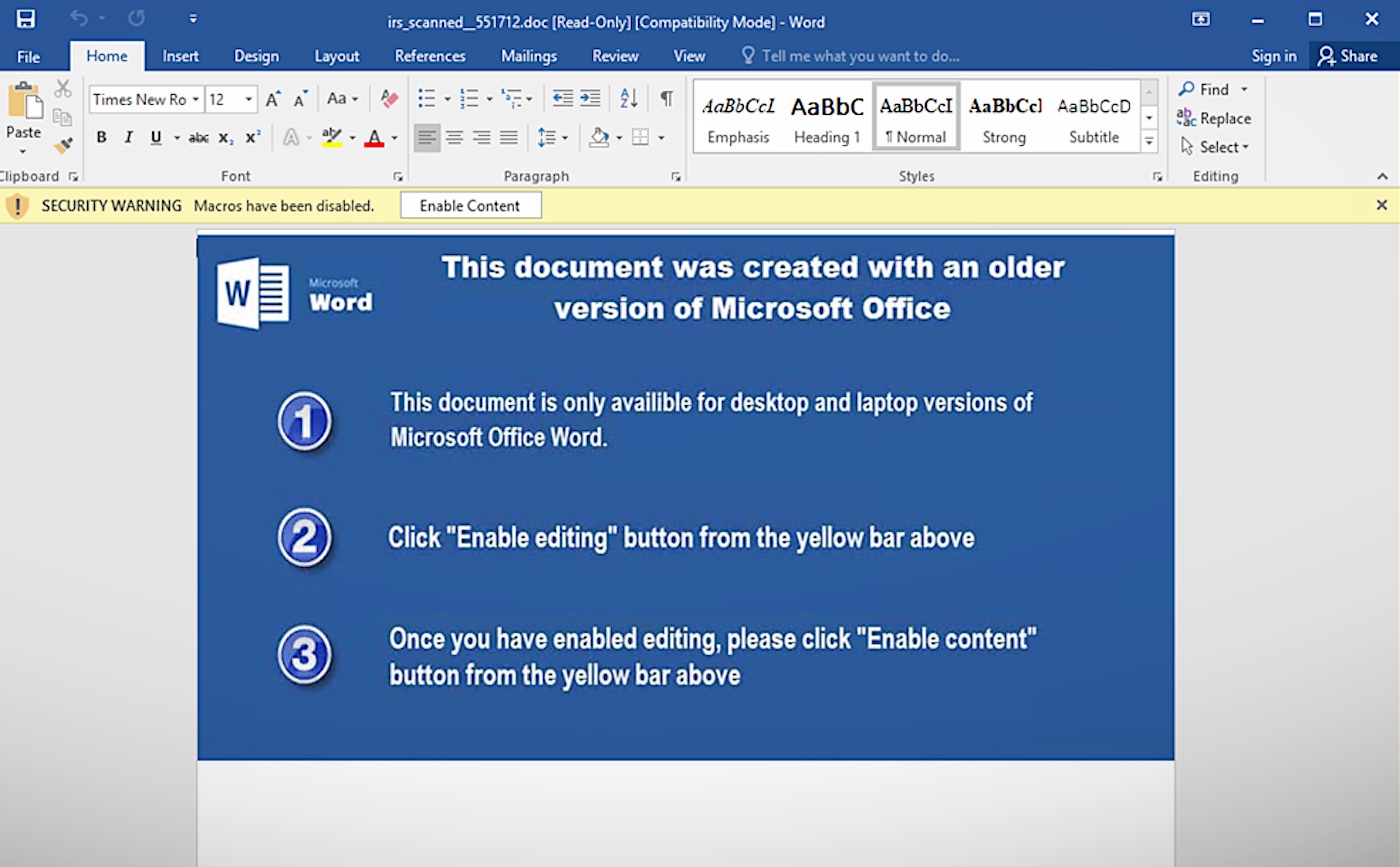
A Microsoft Word document with a malicious macro embedded as part of an IRS-themed malware campaign. Image Credits: Microsoft.
Microsoft said it is still planning to block Visual Basic Applications (VBA) macros by default in Office apps after quietly rolling back the planned change last month.
VBA Macros are lines of code that allow users to automate routine processes — like data collection or running certain tasks — in Microsoft Office applications. While this makes them a handy tool for businesses, particularly those in accounting and finance, macros have long been popular with cybercriminals, who — until recently — could easily embed a malicious macro into a document to deliver malware via email attachments.
Microsoft announced in February, much to the delight of the cybersecurity community, that it would soon block VBA macros sourced from the internet from running by default. The change, which Microsoft at the time said would “prevent users from inadvertently opening files from the internet that contain macros,” was due to take effect in June. But, as spotted by Bleeping Computer, Microsoft quietly rolled back the change on June 30, citing unspecified “user feedback.”
Microsoft faced a barrage of angry comments in Reddit threads and on social media lamenting the change of heart. But the software giant has since confirmed that the surprise U-turn was only temporary, adding that it is “fully committed” to disabling internet macros by default.
“Following user feedback, we have rolled back this change temporarily while we make some additional changes to enhance usability. This is a temporary change, and we are fully committed to making the default change for all users,” said Kellie Eickmeyer, principal product manager at Microsoft, in a blog post update.
Microsoft said in the blog post that users can still block internet macros by changing certain Group Policy settings.
TechCrunch asked Microsoft how it planned to enhance usability and when the disabling of macros would take effect but a spokesperson did not immediately comment.
The move to block macros by default appeared to have been working until Microsoft’s reversal last month. A recent Emotet test campaign observed by cybersecurity firm ESET reveals that attackers may already be moving away from macros-based attacks given Microsoft’s plans to block VBA macros by default. Emotet, a notorious botnet used by cybercriminals to send spam emails, is already replacing Microsoft Word documents with a shortcut file as the malicious attachment.
HP Wolf said in May that it’s also observed a rise in threat actors turning to non-Office-based formats as Microsoft began disabling macros, including a fourfold rise in the use of Java archive files.













 English (US) ·
English (US) ·