
As we close out this year, we’re sharing a number of updates on our work to protect people around the world against various threats.
Since 2017, we’ve taken down and reported on more than 200 covert influence operations, providing details on each network’s behavior so that people know about the threats we see — whether they come from nation states, commercial firms or unattributed groups. Sharing this information has enabled our teams, investigative journalists, government officials and industry peers to better understand and expose internet-wide security risks, including ahead of critical elections.
Here are insights that have stood out to us this year as we look back at our 200-plus CIB enforcements:
The Global Nature of Influence Operations
The CIB networks we’ve taken down came from 68 countries. They operated in at least 42 languages from Amharic to Urdu to Russian and Chinese.
Diverse Targeting By Influence Operations
More than 100 different countries, from Afghanistan to Zimbabwe, have been targeted by at least one CIB network — foreign or domestic — since we began our public reporting. The United States was the most targeted country by 34 operations, followed by Ukraine targeted by 20 CIB networks, and the United Kingdom targeted by 16 operations. Notably, we often saw these covert networks focus on more than one country at a time. For example, one network from Iran we disrupted in April 2020 targeted 18 countries on four continents.
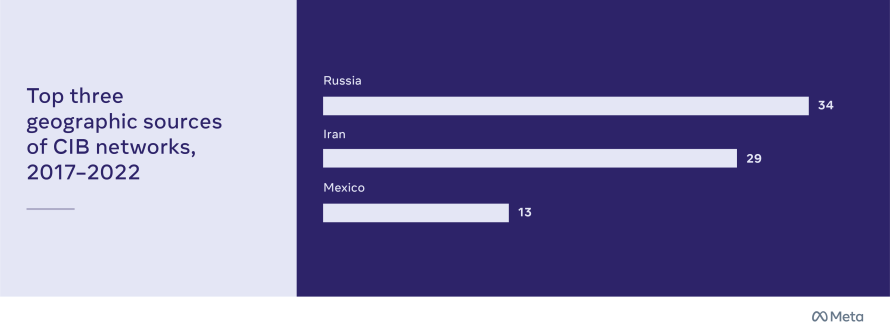
Where Most CIB Networks Came From
Russia (34 networks), Iran (29 networks) and Mexico (13 networks) were the three most prolific geographic sources of CIB activity — whether by state actors, political groups or commercial firms.
The differences between CIB networks in these countries illustrate the complexity of influence operations globally.
Russia: We often hear about the so-called “Russian influence operations playbook,” though our investigations have shown that there is in fact no single playbook relied on by CIB networks originating in the country. The operations we’ve investigated since 2017 varied widely in tactics, targets, complexity, scale and the actors behind them. Since 2017, we’ve disrupted networks run by people linked to the Russian military and military intelligence, marketing firms and entities associated with a sanctioned Russian financier. The smallest CIB network we’ve seen with three accounts only and one of the largest operations we ever disrupted came from Russia: their tactics ranged from spammy comments to running fictitious cross-platform media entities that hired real journalists to write for them. And while most public reporting has focused on various Russian operations targeting America, our investigations found that more operations from Russia targeted Ukraine and Africa.
Notably, both our first takedown and our 200th takedown were of CIB networks originating from Russia. The latter takedown targeted Ukraine and other countries in Europe, which we were able to attribute to two companies in Russia: Structura National Technology and Social Design Agency (Агентство Социального Проектирования), as part of today’s update to our Threat Report from September 27, 2022.
Iran: We’ve seen a diversification in Iranian operations, particularly when it comes to the actors behind the activity. Networks we took down between 2018 and 2020 were mostly linked to government-related entities, particularly state media. Those operations were often centered around websites that promoted content about the Iranian government. Starting early 2021, deceptive campaigns focused more on politics in the target countries and were linked to smaller groups, like academics or people with a background in teaching English as a foreign language, without an apparent link to any larger state entity. This coincides with the US Treasury seizure of domains linked to earlier Iranian operations. This could be a sign of different groups in Iran attempting to run CIB campaigns or change in operational security designed to obfuscate attribution.
Mexico: Most CIB networks originating in Mexico focused primarily on regional or local audiences, often in the context of regional elections. These networks tended to be less tactically sophisticated, and many were linked to PR or marketing firms including instances where one network supported two rivals for the same electoral post. This illustrates the danger of covert “IO-for-hire” services that provide inauthentic support to not just the highest bidder, but multiple bidders at once, polluting the information environment.
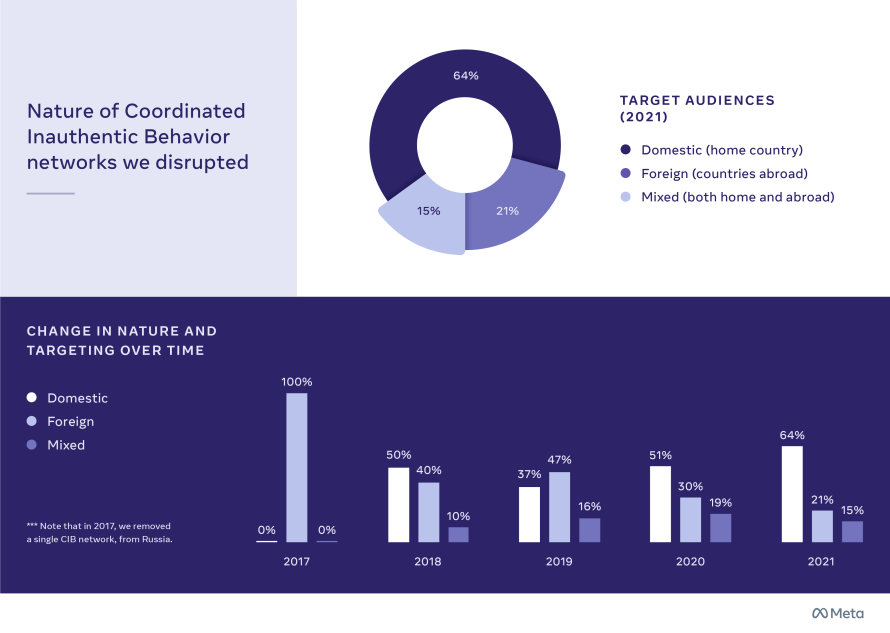
Domestic Versus Foreign Influence Operations
While public discourse around global influence operations often focuses on foreign interference, we found that CIB networks worldwide most frequently targeted people in their own country. For example, we’ve reported on a number of government agencies targeting their own population in Malaysia, Nicaragua, Thailand and Uganda. In fact, two-thirds of the operations we’ve disrupted since 2017 focused wholly or partially on domestic audiences.
The balance between foreign and domestic operations varied dramatically by region. Around 90% of CIB operations in Asia-Pacific, sub-Saharan Africa and Latin America were wholly or partly focused on domestic audiences. By contrast, over two-thirds of CIB networks that originated in Europe and the Middle East and North Africa (MENA) were wholly or partly focused on foreign audiences.
Uniquely, the Gulf region was where we saw covert influence operations from many different countries target each other, signaling these attempts at influence as an extension of geopolitics by other means. For example, we removed: an Iranian network criticizing Saudi Arabia and the US; a network from Saudi Arabia criticizing Iran, Qatar, and Turkey; an operation from Egypt, Turkey and Morocco supporting Qatar and Turkey and criticizing Saudi Arabia, the United Arab Emirates (UAE) and the Egyptian government; and a network from Egypt supporting the UAE and criticizing Qatar and Turkey.
The Cross-Platform Nature of Influence Operations
We’ve continued to expose operations running on many different internet services at once, with even the smallest networks following the same diverse approach. For example, in 2020 we took down 10 accounts from Russia that targeted Turkey and Europe. In 2021, we took down four accounts from Iran. In January we took down three accounts from Russia. In each case, while their activity on our platforms was minimal, they each ran “news” websites and targeted other internet services. We’ve seen these networks operate across Twitter, Telegram, TikTok, Blogspot, YouTube, Odnoklassniki, VKontakte, Change[.]org, Avaaz, other petition sites and even LiveJournal.
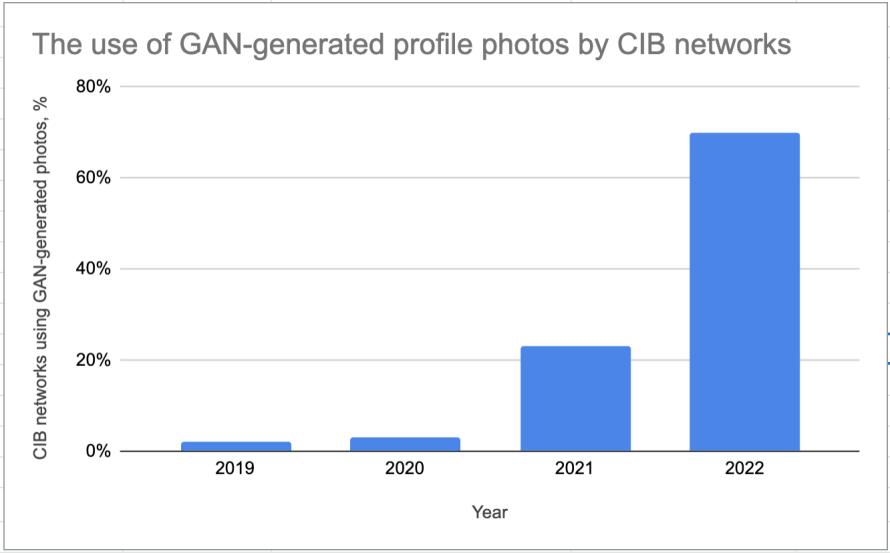
Use of AI-Generated Profile Photos
Since 2019, we’ve seen a rapid rise in the number of networks that used profile photos generated using artificial intelligence techniques like generative adversarial networks (GAN). This technology is readily available on the internet, allowing anyone — including threat actors — to create a unique photo. More than two-thirds of all the CIB networks we disrupted this year featured accounts that likely had GAN-generated profile pictures, suggesting that threat actors may see it as a way to make their fake accounts look more authentic and original in an effort to evade detection by open source investigators, who might rely on reverse-image searches to identify stock photo profile photos. However, our CIB enforcements focus on behavior rather than the content posted by these networks, including their photos. In fact, in our CIB investigations, we look at a combination of behavioral signals which means that the use of GAN faces does not help threat actors to evade enforcement.
For more information, see our past threat reporting.
The post Recapping Our 2022 Coordinated Inauthentic Behavior Enforcements appeared first on Meta.















 English (US) ·
English (US) ·